Who is responsible for Cyber Security?
Many organizations today are fueled by information. The more business-critical information is, the more damage threats can do. The threat landscape today is more complex, and cyber criminals are well organized.
It has probably never been as relevant as it is today to make sure that you work in a structured manner (i.e. implementing an Information Security Management System – ISMS) to identify, protect, detect and recover from breaches or other abuse from external, or internal, sources.
With that being said, the short answer to the headline question is everyone in the organization has a responsibility for upholding their part of the security. The human factor is key. Cyber security is the combined application of technology, processes, and controls, and the key enabler for achieving this is the human factor. If we as an organization lack awareness and do not understand the complexity and risks that we are exposed to, it can (and probably will) be the factor that enables cyber-attacks despite all technical measures implemented to avoid them.
We have defined three responsibility areas:
- Management
- The user
- Technical personnel
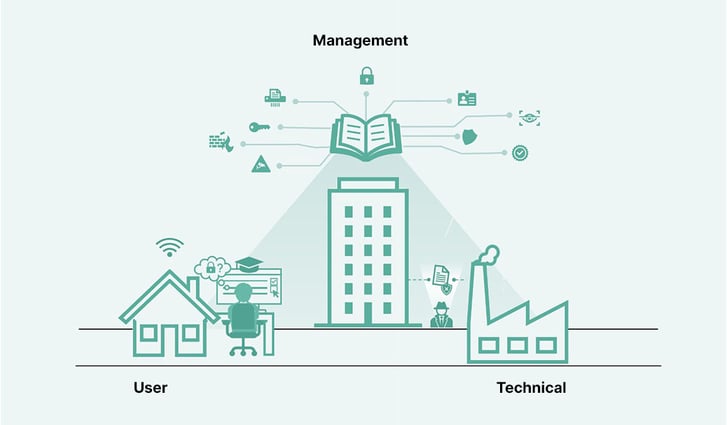
Management is responsible for the organization's combined security performance, including vendors and partners, as well as the internal organization. Management defines the security scope, roles, responsibilities, and mandate, and is responsible for funding the cyber security work. Through control mechanisms, management ensures insight as a decision basis to establish and maintain an acceptable risk level.
Users are responsible to take part in training programs and understanding and follow the governing rules and procedures of the company. Users should be able to detect and avoid attacks and report incidents and concerns.
Technical personnel is responsible for ensuring that the organization has a secure technical architecture according to the decided risk level. The IT department must translate business targets, processes, rules, and policies into technical implementations. Tech personnel are also responsible for monitoring day-to-day operations and evaluating and managing tech changes from a security perspective.
How to get started?
If your organization has not set any rules and responsibilities regarding security – it is time to do so. It is not 'the IT guys' alone that are responsible. Struggling with where to start? A general tip is to start ‘top-down’ by setting the scope and establishing roles with capacity and relevant competence for the organization's security ambitions. The security work should be structured in an Information Security Management System to ensure efficiency and that measures are based on cost/benefit assessments and prioritized to best support business goals.